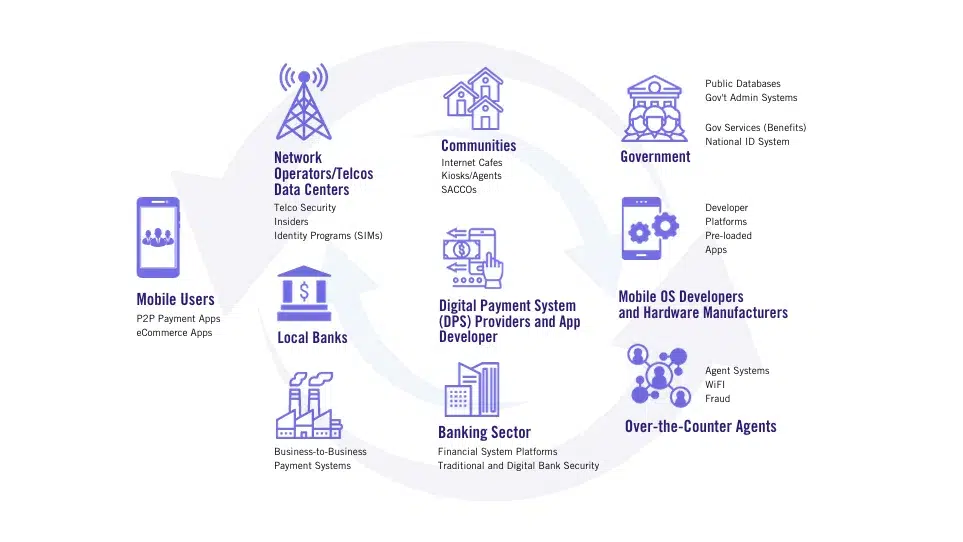
Securing the Digital Financial Ecosystem Abroad

As described in our overview post on evaluating mobile security technologies, we are releasing a blog series to bring the community up to a collective understanding of the mobile threat landscape, explain our current thinking on evaluating mobile security products, and solicit feedback on both mobile threats, as well as evaluation methodologies for the domain.
This post explores the second of four mobile threat scenarios: phishing threats against mobile devices. In addition to describing the threat, we outline potential approaches for evaluating mobile security product capabilities, challenges that exist, and areas where we could use community input.
We invite feedback from the community on all aspects of this research, whether better insights into the threats that need to be defended against, types of products to evaluate, or how to evaluate technologies against these threats. Please reach out to the ATT&CK Evaluations team (evals@mitre-engenuity.org) with any comments or questions you might have to help shape our future work in this space.
Read the full Medium blog post